Making Web3 More Human: Proof of Humanity
Proof-of-Humanity specifically addresses the need to verify that an entity is indeed a human, not a bot or automated system. This verification is crucial in ensuring that interactions within decentralized networks are authentic, trustworthy, and aligned with the principles of fair participation.
In this context, Proof-of-Humanity can be seen as a subset of a more extensive concept known as “Proof-of-X.” This concept refers to the validation of various identity attributes based on specific evidence or activities. For instance, Proof of Responsibility validates that a user holds x creds or privileges, while Proof of Reputation can verify a user’s credibility based on their past behavior within a network.
Each of these proofs offer a more detailed and reliable understanding of who or what is interacting within a decentralized system. These Proof-of-X approaches, particularly Proof-of-Humanity, are essential for maintaining the integrity, security, and fairness of digital ecosystems while prioritizing decentralization and user autonomy.
The Importance of Proof-of-Humanity in Web3
The risk of bots and malicious actors exploiting your systems is directly proportional to the growth of your system. Verifying that participants are real humans is crucial to maintaining a level playing field, where only legitimate users can engage in activities such as voting, governance, and earning rewards. Other key benefits:
1. Prioritizes Genuine Love Over Farming
The most valuable users are the ones who love what you’re building, not those looking for a quick win. PoH weeds out temporary “farmers” and rewards the ones who care. This builds a loyal base that’s invested for the long haul, not just for the next reward.
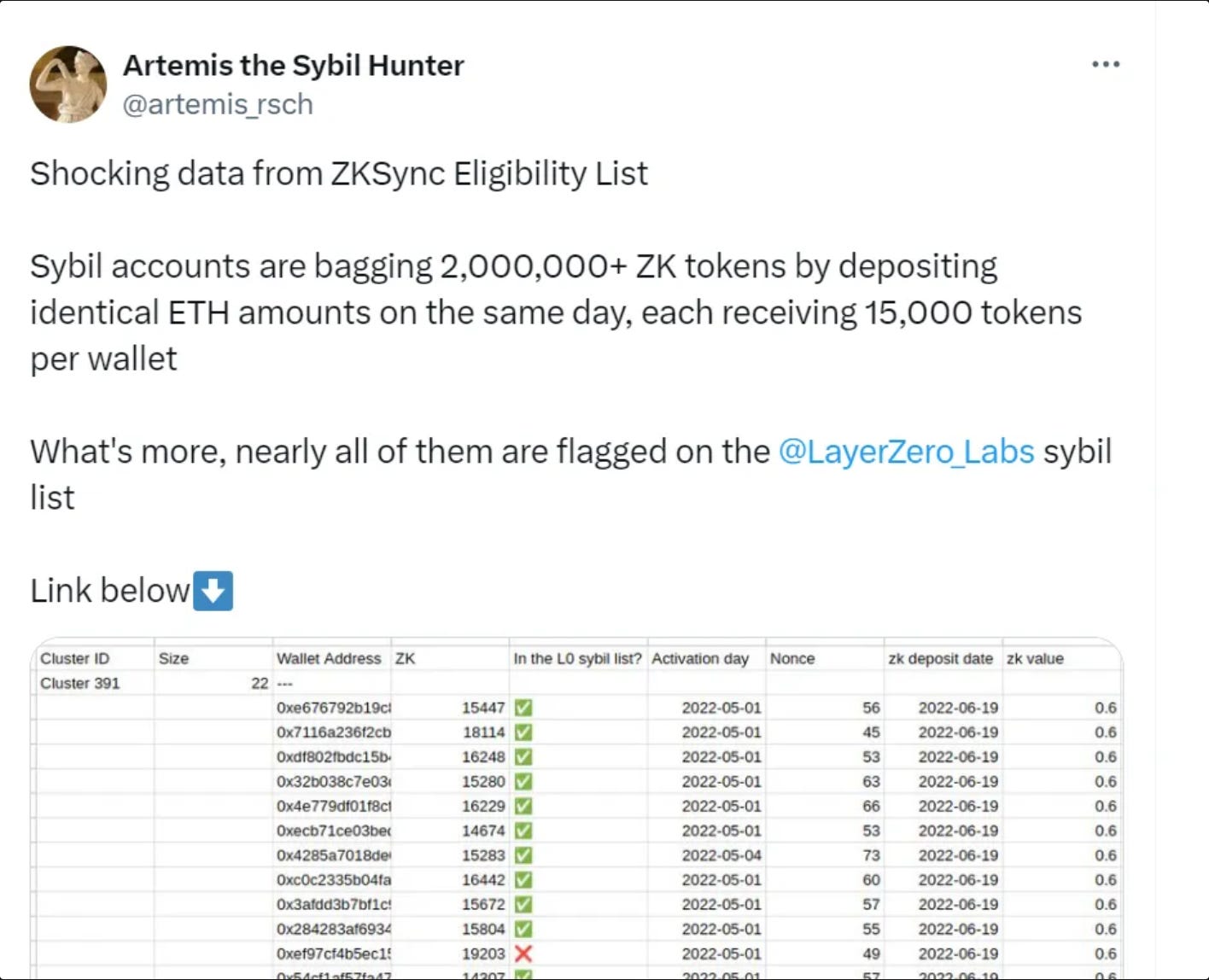
Example: ZKSync’s eligibility list led to backlash from users who felt sidelined. People get upset when they feel overlooked or treated unfairly. That’s avoidable, and PoH can help.
2. Strengthens Retention Post-TGE
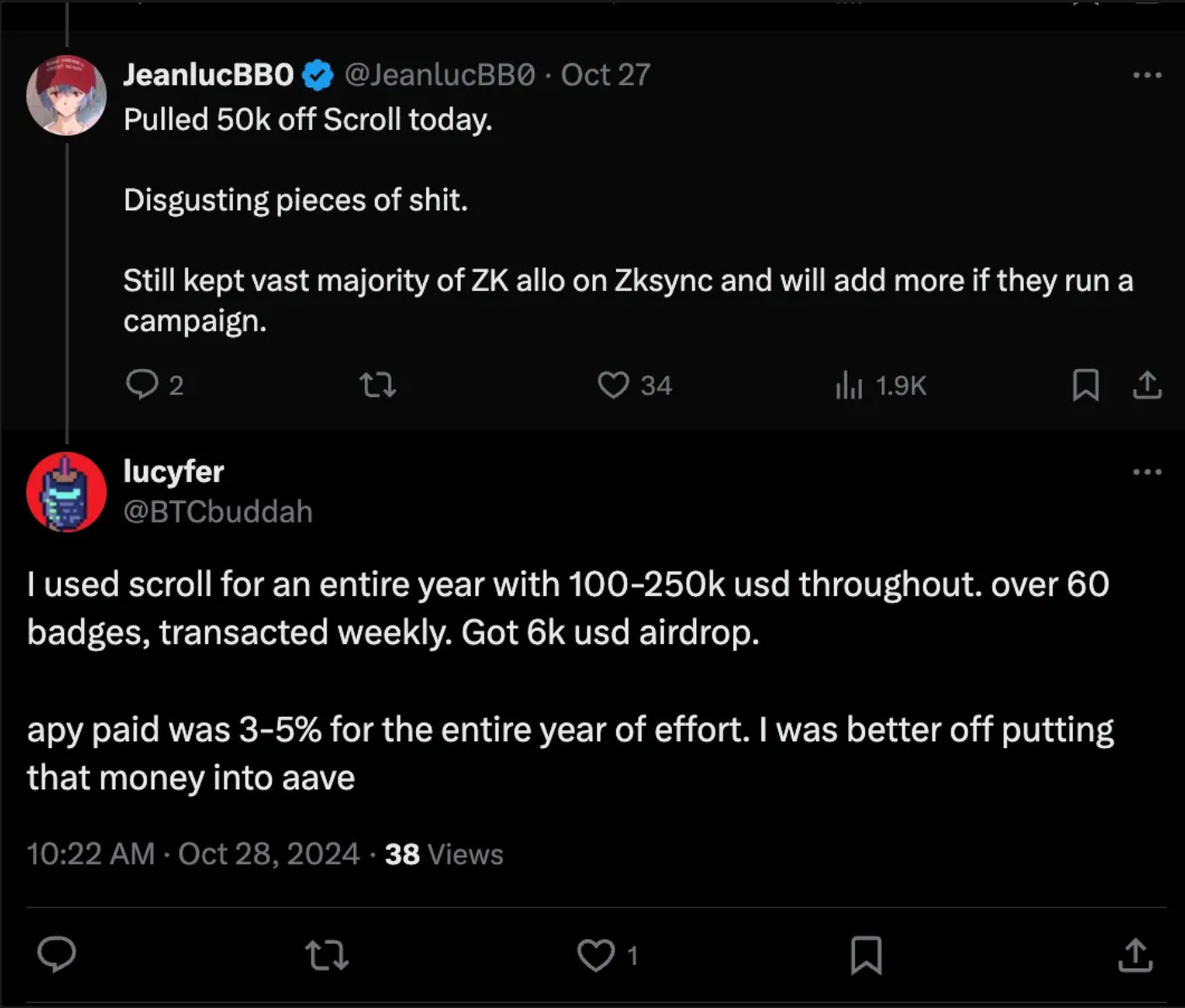
After an airdrop, many projects face a sudden drop-off. This happens even to great projects(like Scroll). PoH helps maintain retention post-TGE by keeping holders who genuinely believe in the project. A steady, stable community is better than one that spikes and drops on a whim.
Curbs Bot Activity and Ensures Real User Access
PoH filters out bots and low-effort participants, especially during early access or exclusive releases. This ensures that only real users—dedicated to the project—can participate, enhancing community quality and engagement.
Builds a Richer, More Trustworthy Community
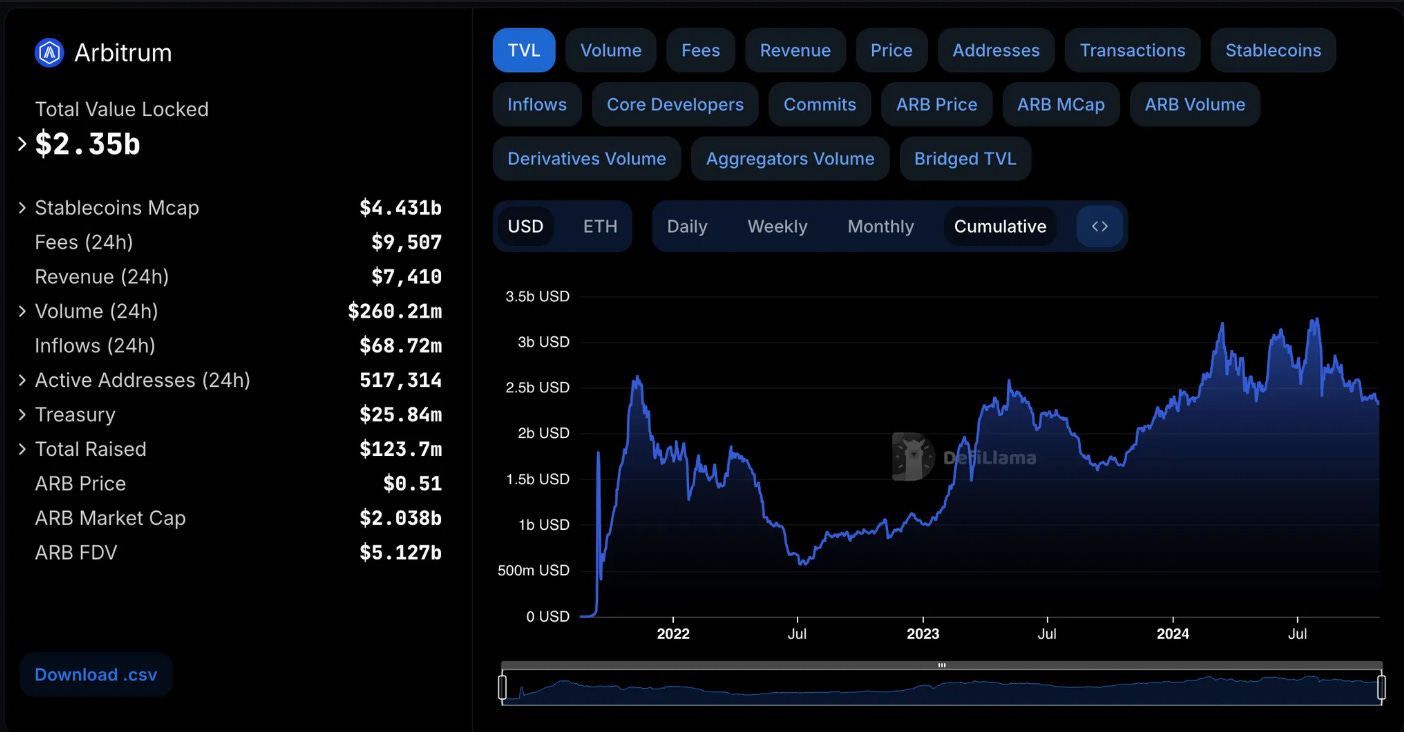
Arbitrum saw a big spike in TVL post-airdrop. This indicates that airdrop users found ongoing value in the ecosystem and stuck around. PoH lets you see who’s genuinely engaged.
These are the users who add value to your project, who contribute meaningfully, and who stay for reasons beyond a reward. With a verified base, projects can foster real relationships, build trust, and celebrate true supporters.
Protects Token Price with Real Supporters
PoH helps you avoid the quick dump-and-run that often follows a TGE. When only committed participants are rewarded, the token price holds up better because it’s not at the mercy of speculators looking to cash out.
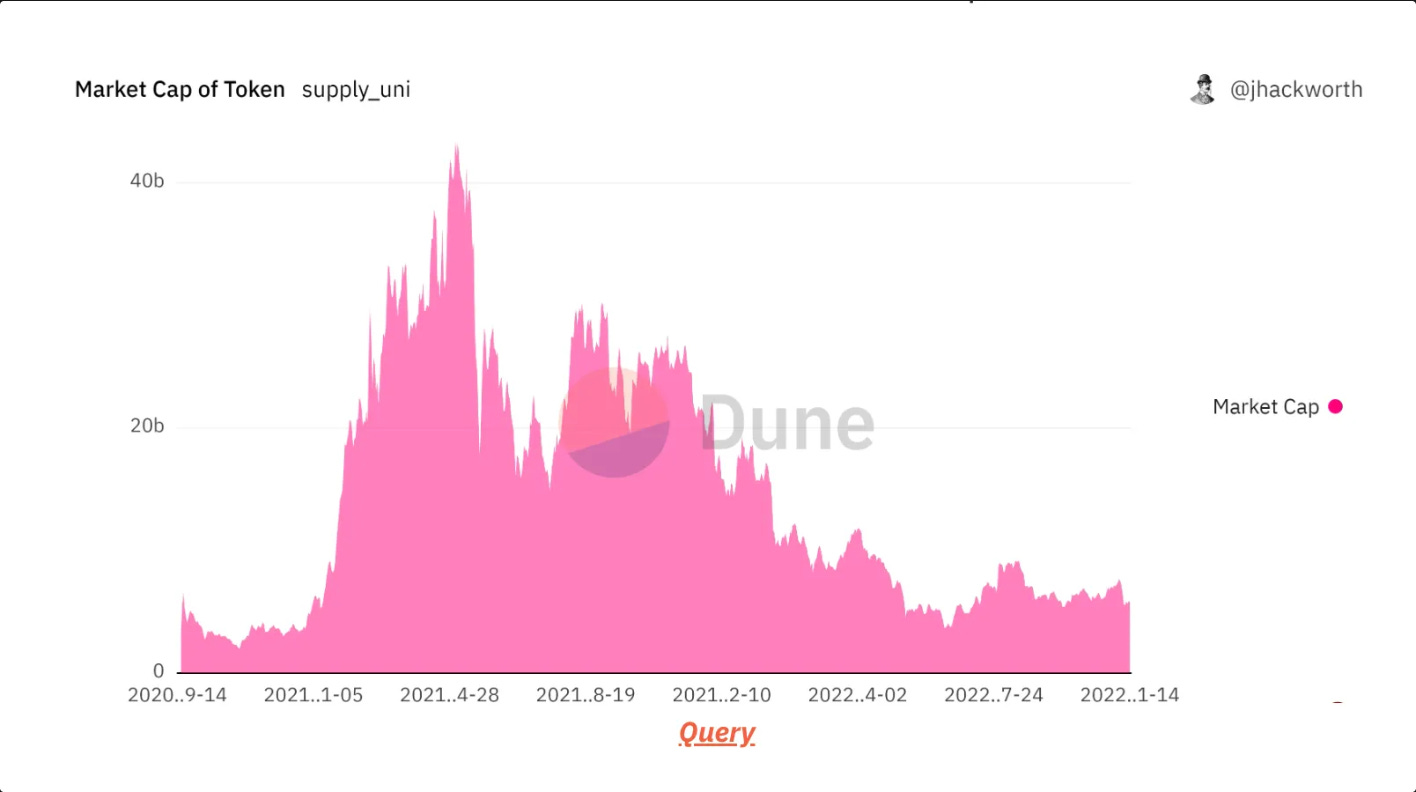
Look at Uniswap: Its market cap dropped right after its airdrop because too many people were in it just for the quick sell. If you can keep bots and sybils out, you reduce volatility and protect your project’s value.
Deconstructing Digital Identity: The “Proof-of-X” Framework
Digital identity isn't monolithic; it's a collection of evidences from various online and offline activities. This can be conceptualized through the "Proof-of-X" framework, where each "X" represents a different identity attribute validated by specific activities.
Core Components
Identity is built from observable or inferred behaviors, such as social media participation, online shopping, blockchain transactions, and attending events. These activities generate data points that collectively shape a comprehensive digital identity.
Activity-Based Identity Construction
Different activities contribute to different identity aspects. For example, frequent online shopping indicates an active consumer, while social media engagement suggests high social interaction. In Web3, participating in DeFi, voting in governance systems, or contributing to DAOs adds layers to one's digital identity.
Evidences as Active Validators
Evidences actively validate identity attributes. "Proof of Reputation" might come from community interactions, while "Proof of Responsibility" could be validated by roles in organizations. This creates a multi-dimensional, evidence-based identity continuously verified by actions and interactions.
Decentralized Validation
Trust is decentralized, and identities must be validated without central authorities. Viewing identity as a set of evidences helps create robust, nuanced, and trustworthy digital identities reflecting true individual nature in a decentralized environment.
Categories of Proof-of-Humanity and Related Solutions
Before diving into the specific categories of Proof-of-Humanity, it’s important to recognize that the definition of “humanity” can vary depending on the application. For instance, an application distributing Universal Basic Income (UBI) requires a stringent Proof-of-Unique Human to ensure that each individual receives benefits fairly, without any duplication.
On the other hand, a gaming platform might be more concerned with preventing abuse rather than verifying uniqueness. In such cases, the game may tolerate a few accounts per user, allowing for flexibility in gameplay, but still needs mechanisms to prevent mass account creation by bots or automated systems.
This variance in requirements highlights the need for tailored Proof-of-Humanity solutions that align with the specific goals and contexts of different Web3 applications.
Proof of Unique Human
Biological Solutions
Biological solutions use biometric data such as fingerprints, iris scans, and palm prints to verify the uniqueness of an individual. These methods are highly reliable as they are based on physical characteristics that are difficult to replicate.
Examples:
Worldcoin: Utilizes iris scanning to create a unique digital identity for individuals on a global scale, aiming to democratize access to the digital economy.
Humanity Protocol: Leverages biometric data to ensure that each identity in the system is linked to a unique human being.
National Identities/KYC
This approach involves using government-issued IDs, such as passports or Aadhaar, for identity verification. These documents are widely accepted and provide a high level of trust in verifying that an individual is a registered citizen.
Examples:
Galxe Passport: Utilizes KYC procedures to verify the identity of users, linking their national identity to their digital presence in the Web3 space.
Proof of Responsibility
In Web2, Proof of Responsibility can be demonstrated through domain-specific logins or IP whitelisting for API usage, ensuring that access is granted only to authorized entities.
Web3 Examples:
Linea’s Account Linking: Allows users to link multiple accounts for airdrop eligibility, ensuring that only responsible users with consistent participation are rewarded.
LayerZero’s Auto Sybil Declaration: Automatically detects and declares Sybil attacks, where one user tries to illegitimately claim multiple identities.
Proof of Reputation
Reputation plays a crucial role in verifying trustworthiness. Systems track the behavior of participants to assess their reputation within the network.
Public Databases of Bad Actors: Tools like LayerZero’s Sybil list track known bad actors, preventing them from manipulating the system.
Web3 Scores: Platforms like Nomis assign scores based on user activity across different chains, considering factors such as whether a user has sold past airdrops, which could indicate opportunistic behavior.
Social Score Solutions: Platforms like BrightID utilize social graphs to verify reputation based on community trust and interactions.
Proof of Humanity
Captcha solutions involve challenges that are designed to be solvable only by humans, thereby preventing bots from accessing certain services.
Examples:
Idena: Uses AI-generated puzzles as a form of captcha to verify that participants are human, ensuring that only real people can engage with the platform.
Webcam-Based Verification This method requires users to perform specific human-like movements or expressions on camera, which are difficult for bots to mimic.
Examples:
Humanode Bot Basher: BotBasher uses confidential facial recognition technology to confirm the unique identity of each user.
Human-Like Behavior Detection These solutions analyze patterns of activity that are unlikely to be automated, such as late-night food orders or diverse app usage, to verify human identity.
Examples:
Behavioral Clustering: By analyzing activities across different platforms, this method clusters behavior that is typically human, distinguishing it from automated or bot-like patterns.
These diverse approaches to Proof-of-Humanity and related identity solutions in Web3 highlight the importance of verifying not just the existence of a digital identity, but also its authenticity, uniqueness, and trustworthiness. As these methods evolve, they will play a crucial role in shaping a more secure and equitable decentralized ecosystem.
Challenges and Opportunities in Proof-of-Humanity Solutions
PoH systems in Web3 are tackling one of the hardest problems out there: verifying identity in a world built to be anonymous and decentralized. But to get to the future everyone talks about, PoH needs to overcome some critical roadblocks:
Fragmentation:
PoH systems don’t talk to each other, or to the many platforms and wallets people use. Each PoH solution is like an isolated island. To make these systems truly useful, they need to be part of a larger, unified ecosystem where your identity is recognized everywhere, without extra friction.
Interoperability:
Right now, PoH solutions are too siloed to work across the broader Web3 space. If a PoH solution only works with certain dApps or chains, its utility is limited from the start. Compatibility has to be the default, not an afterthought.
Incomplete Data Reliance:
Most PoH systems rely on either on-chain or off-chain data, but both approaches have limitations. On-chain data is secure but narrow, and off-chain data is more comprehensive but lacks immutability. PoH ne eds a balanced model that combines the reliability of on-chain with the richness of off-chain.
High User Effort:
PoH is far too complex for most users right now. Managing keys, going through repeated verification, navigating clunky UIs—these are pain points that prevent mass adoption. If PoH is going to go mainstream, it has to be as easy as opening an email.
Inconsistent Standards:
Different platforms have wildly different ideas about what constitutes a “real” user. Without a universal standard, we’ll continue to have fragmented systems that don’t interoperate. PoH needs a shared baseline of what “human” means in a Web3 context.
Opportunities for a Smarter Proof-of-Humanity Ecosystem
As tough as these problems are, they’re also opportunities. Here’s what could happen if the Web3 space tackles these issues head-on:
Cross-Ecosystem Integration: Imagine if a single PoH verification worked everywhere—your identity was recognized across all platforms and wallets. This is about building a true “Web3 passport,” giving users a seamless identity experience across the entire ecosystem.
Hybrid Data Models: PoH systems that combine on-chain and off-chain data could finally bridge the gap. The goal here isn’t just to be secure or flexible—it’s to be both. When PoH solutions strike that balance, they’ll be far more valuable and trusted.
Improved UX: We need to make PoH invisible in all the right ways. The best user experiences are the ones you barely notice, and PoH should be no different. If it’s as easy as logging in to your favorite app, it’ll reach a broader audience, including non-technical users who won’t touch it now.
Global Inclusivity: The best PoH systems will work everywhere, not just in the US or Europe. Building with global relevance in mind will make PoH far more valuable to the broader Web3 audience, especially in regions where centralized identity systems are weak or absent.
Democratized Verification: PoH solutions should put users in the driver’s seat, letting them define what “verified” means for them. This isn’t just about inclusivity; it’s about building trust. If users feel they control their identity in the system, they’ll be far more likely to adopt it.
By addressing these challenges and capitalizing on these opportunities, the Web3 community can develop more reliable, user-friendly, and inclusive Proof-of-Humanity solutions that enhance the integrity of decentralized platforms. If you're still reading you'll probably want to read our this other blog on Intract's Proof of Humanity solution.